Fundamentals of Operations Security
The first rule of prep club is…you don’t talk about prep club. The second rule of prep club is…you don’t talk about prep club.
Operations Security, or OPSEC is an essential part of every preparedness minded person life. OPSEC is the process of identifying and limiting potential vulnerabilities in security that may lead to enemies compromising your safety. If the proverbial Stuff Hits The Fan, the last thing you want is people knowing that you have a good stock of supplies, or where you have hidden them. This means limiting who knows about your prep, and ensuring that they also keep things secret.
The Five Steps
There are five steps to the operations security process, the first is to identify critical information. This includes your location, security system, capabilities, limitations, and your inventory. It also includes personal information about everybody in your mutual aid group, or any other information an enemy may find useful. After you have identified the critical information, you need to be very careful not to give indicators to people that may reveal this information. Indicators are words or phrases that may clue people in on what is in your prep, and should be avoided, and sudden changes in your behavior, especially when doing something like buying supplies, should be minimized, for example; rather than place one large order of supplies, try making several smaller purchases. Do not take the exact same route when rehearsing your bug-out routine, as this could enable people to follow you and locate your stash or hideout.
The second step in the operations security process is to analyze potential threats. Try and determine if any people pose a hazard to you, whether that threat is physical, or simply that they give away too much information to others. For example, you may have a good friend that tends to let things slip in conversation, or makes social media updates revealing personal information. Although that person poses no physical threat, you will probably want to limit what information they have so that someone who IS a threat does not find out critical information.
Risk
The third step is to analyze vulnerabilities in your security. Vulnerabilities are anything that may possibly allow someone to access your information, whether deliberately or intentionally. Things like discussing sensitive information in public are very risky. Try to only discuss critical information privately, and in person, as phone calls or email can be intercepted. Shred paper items that may disclose sensitive information before discarding them. Limit what you reveal on social media sites. Try not to post personal photos that may reveal your identity or location; that family photo in front of your new house or vehicle may be exciting to share, but it could easily reveal your identity and where the photo was taken. Easily recognized landmarks are also a big giveaway as to your general location.
The fourth operations security process is to assess those risks. Are you giving away any indicators in your behavior or conversations? how would an enemy benefit from the information you have, and how would that impact your safety? are there any negative effects from keeping certain information hidden? for example, if you have a bug-out location ready, will you tell your friends and family members so they can get there if you become separated, or will you be the only one that knows? keeping that information to yourself may mean that some of your loved ones become separated from you, maybe permanently. On the other hand, if you tell them, someone may inadvertently disclose your location to others and put you at risk.
Finally, you will need to apply operations security countermeasures to ensure your safety. The easiest precaution to take is to not discuss your information at all, but in instances where disclosure is necessary, you should try to conceal any indicators, and make them appear unimportant. Don’t make predictable behavior patterns, and try to protect critical information as much as possible.
Securing Your Digital Data
“Never type anything into your keyboard that you don’t want published on the home page of a major news website”

Securing your digital data starts with securing the equipment that you use to store and transmit it. Maintaining access control to that equipment is essential. You will want to restrict access to only trusted parties through the use of locks, passwords that are changed every three to six months, live monitoring, etc. Having a secure computer starts with secure software. The best software is open source because it is peer reviewed, and we recommend that anyone that is truly serious about their security use a Linux distribution for their operating system. There are very few things that you can do on Windows that you can’t do with Linux. When the time comes to dispose of your computer, while there is software available to overwrite data, the best option is to completely physically destroy the hard drive.
Some of the threats that operating in a digital space makes you vulnerable to are: hackers, law enforcement, mass surveillance such as the NSA, burglars, identity thieves, scammers, and people less prepared than you that might want to take advantage of your forethought. Some of the best practices for maximizing digital information security include ensuring that you have a firewall and an updated malware program, and using browser plugins to block flash and scripts by default and HTTPS Everywhere to reduce the chance of running malicious scripts, and to force websites to encrypt traffic respectively. If information is particularly sensitive, use an anonymizing protocol such as TOR or a VPN, and use GnuPG to digitally sign and encrypt private emails. If you must use WI-FI, it is best to not broadcast your SSID, and to use the highest level security available with AES encryption and a very long key that includes multiple capital and lowercase letters, numbers, and symbols. It is not unreasonable to have a WI-FI key that is in excess of twenty six characters.
When using social media, blogs, forums, or other sites featuring user generated content, remember that access control applies here as well. Use a password with multiple capital and lowercase letters, numbers, and symbols, and that is different to all your other passwords. Ensure that you read the terms and services thoroughly and that you are comfortable with what information they give away or sell to third parties. Take care when filling out web forms to make sure you are on a trusted page and not a phishing site, and check your privacy settings frequently to be sure that they have not changed. When clicking on links, make sure that you trust the host and webmaster with your IP address, as it can potentially be used to geolocate or DDoS you. Many people that will try to exploit you will pretend to be your friend or somebody you know. This is a common practice known as catfishing, so be sure any friend requests you receive are thoroughly vetted, and be most skeptical of contact from people you think you may know.
When posting images online, always use an image editor such as GIMP to scrub the image of EXIF data or black out critical information from pictures and documents before posting. When taking selfies or other photographs, always be mindful of the background of the image that may reveal your location, identity or other vulnerabilities such as prominent land features, house numbers, or the license plate of your car. Be aware of reverse image search, for example: if you post a picture in a forum that is also featured on a site where you list personal details, it may be used to link different profiles that you may not want linked.
For the same reason that you would not want your house number visible in a picture, you should also not post your address or personal phone numbers in any public space. Additionally, you should not post the names of your children or the school they attend (I would be reluctant to even post my dogs name). Use discretion when naming your employer or job description, especially if your job provides you with unique access. Never post the dates, locations, and times for planned vacations or extra curricular activities. Under no circumstances should you ever let the world know that you are away from home or your that children are alone.
Families and OPSEC
As a preparedness minded person, your family and close friends should all be a part of your operations security plans. The concept of the circles of trust breaks down people that you routinely contact into six groups, based on how much access they have to information about your plans and capabilities. The top three inner circles are made up of the head(s) of household, those under their direct care, and close family and friends. The responsibility of the head(s) of household are to be magnets of information gathering, and to control who receives that information. Ultimately they have the most to lose if safety measures are compromised. They are also responsible for the delegation of tasks and responsibilities.
Grandparents and Children
Dependents make up the second circle, and although dependents are usually children, can also be the elderly, ill, or anyone cared for by the head(s) of household that rely on them for some or all of their needs. Due to their close dependency, this group is usually forced to be privy to sensitive information, routines, and most of your preps. It is often difficult or impossible to conceal aspects of your provisions.
You don’t need to lie to children to keep your operations secure, but that doesn’t mean you have to tell them everything either. Kids are brutally honest, and lack discretion, especially the young ones. In the gun control debate(s) of 2013, kids all over the country were being asked whether or not their parents owned guns by people they trust, including teachers and doctors. While it is important to teach kids valuable skills, it is more important to protect yourself against your kids inadvertently revealing your prep.
all of the same steps that we suggested in the above section to protect your social media identity should be taught to your children as well. The best way to ensure your child keeps information within the inner circle is to scare them with a worst case scenario. Explain to them that there are people that will take your supplies, or potentially hurt or even kill you to take what you have if they know your prepping plans. Create hypothetical situations with children to role play different scenarios that they may find themselves in to help them develop strong responses to potentially dangerous events. For example, rehearse with them what would happen if a stranger knocked on the door and asked to come inside to use a phone, or what they would do if someone like a friend or teacher asked about guns, money, or other supplies. Have a plan for what they would do if somebody kicked in the door in the middle of the night, or if the fire alarm goes off, or if their caregivers are arrested.

You should have family code words that everybody understands, and knows to keep only for use in the inner circle. When a child is really young, it is easy to spell out words you don’t want them understanding, but as they get older it is often a good idea to have code words for sensitive topics so that your kids don’t accidentally discover them. Using a code word for when your child is talking too much about private information lets your child know to be quiet. If you have to send a stranger to pick up your child, instruct them to provide a countersign when given one by your child, and the words should be completely random and unrelated.
EXAMPLE:
Stranger: “Your mom sent me here to pick you up.”
Child: “butterfly”
Stranger: (The stranger actually knows the parents and is telling the truth)”Watermelon”
In this scenario, if the stranger looks confused, or says anything other than the countersign, your child will know to run. Countersign code words can be worked into a sentence if other people are around to hear. You can also use countersigns to signal that you are in danger.
EXAMPLE:
You have set up a code word that includes green things to indicate safety, and red things to indicate danger. Someone breaks into your home, and you all rush to a safe room, however one of your children lagged behind. You hear a knock on the door and want to know whether it is safe to let them in, or if they are being held at gunpoint…
You: “How are you doing?”
Child: “I would really like some spearmint gum”
In this scenario, you will know that your child is safe, because spearmint is green. Conversely, if the child had replied ” I would like some cinnamon gum”, you would know that it is not safe to open the door.
EXAMPLE:
Your home has been invaded, and your children have locked themselves in a safe room. You knock on the door to be let in
Child: “have you seen my red sweat shirt?”
You: “Yes, I thought I saw it in the bathroom”
In this scenario, your child not only knows to not open the door, but that the danger is in or near the bathroom.
The third inner circle from the center is close family and friends. These are the people that you will probably invite in your home regularly, or you may ask them for help with some aspects of prepping such as harvesting produce, or maybe you introduce them to some prepping concepts. Some of these people may even make up the core of your mutual aid group. These people are not trusted as much as your dependents because they are not with you all of the time, but if the stuff hits the fan, these people may come knocking on your door, whether invited or not. They will obviously have some basic knowledge of your prep, such as that you have a large store of food, or that you have space in your basement to hold extra people, but you should do your best to limit what they know, and never tell them specifics such as the location of your food supplies or where your bug-out destination is.

Grey Man and OPSEC in Public.
The most important thing to remember about keeping operations security in public is DON’T STAND OUT. We notice people due to a distinct look, smell or sound, or some action that causes us to think. In a disaster there are some things that you just do not want to smell like, such as food, gunpowder, soap, or blood, as these can all be indicators that your situation is better or worse than theirs. All indicators can be bad, but indicators that evoke desire can be extremely dangerous. Whether it is someone talking loudly or rudely, someone wearing dirty clothes, or even just someone that happens to resemble someone you know, or is wearing the same clothing as you. Once a person has been noticed, their Operations security has already started to be compromised.
Don’t wear clothing that stands out. If you are over-dressed in a casual environment, everyone will notice, much the same as dressing in scruffy attire or mismatched colors will draw attention. Don’t wear anything that is too old, too new, too tight, or too loose. Clothing with bright colors or logos will also attract attention quickly, and any clothing that features your name such as a high school sports team jersey or a bowling shirt could compromise your identity, and potentially open a security hole, as well as make you more memorable – none of which you want.
There is something to keeping up with the Joneses.Your home is your castle, but it should not stand out like one. The last thing you want is it giving off the appearance that you have valuable items inside. Make sure your house blends in with others on the street.Having a perfectly manicured lawn in a neighborhood where people only mow monthly will stand out as equally as letting your garden grow wild, so be sure that it matches your neighbors. Some things to try to avoid would be political signs or excessive holiday decorations. Having an attached garage is a bonus, because it allows you to load and unload your vehicle without being watched.

Collect packages soon after they are delivered, and don’t leave mail in your mail box as it is a prime target for identity thieves. If you want a large water storage, a swimming pool will blend in with a suburban house, and a large water tank would not be out of place in a rural setting. If you must build an underground bunker in suburbia, at least have a garden or a wine collection so that it can easily be explained as a root or wine cellar, and build a shed, greenhouse, or gazebo over the top to conceal the entrance.
In the same way that you do not want your house to stand out, you do not want your car to attract attention either. Using your bug-out vehicle as your daily driver is NOT recommended. When you are in a public parking lot, do not park too close to the store, and don’t take up more than one parking space. Make sure that all of your lights work, your tires are all pressurized, and that there are no cracks in your windows. Choose a vehicle with neutral colors such as black, white, beige, silver etc. Having the rear windows tinted will help maintain privacy for your cargo and passengers. Don’t display stickers on your car, especially ones that may reveal information about you (this means you, with the Gadsden flag).
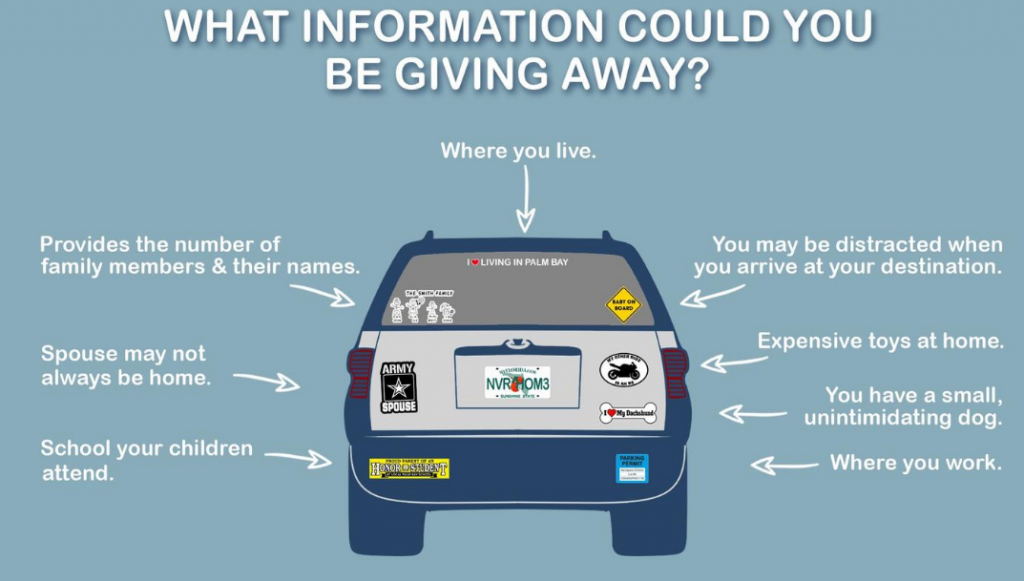
Take Suzy Q Soccermom’s mini van for example. It has one of those stick figure families on the rear window that shows us that her son likes soccer, her daughter likes ballet, and she has a new baby, a pro life sticker suggesting her political leanings and possibly her religious ones as well, one from her sons school showing not only that he is an honor student but where he is available to be kidnapped 5 days a week, and a big old jesus fish above the personalized plate that says “SUZYQ”. While Suzy may be proud of her family, she does not realize that everyone she drives near now knows exactly how many people are in her family, which school her son attends, and that she will likely be away from the house to attend church for a couple of hours on Sunday. If her political party is known for being anti-gun, they will also reasonably expect that her home will not be defended even if she is there.
When you put on your grey man work clothes, get in your grey man vehicle, and go to your grey man job, don’t display personal things that may disclose that you are a prepper or survivalist at your work station such as your “I heart bushcraft” mug that’s holding your pens on your desk, or that photo of yourself at the tactical firearms training school. While putting up a photo of the family isn’t going to be as dangerous at work as it would be on social media, you should still use discretion.
Avoid discussing any survivalist topics around the water-cooler or at lunch break. Many people hearing things like that will think you are a bit crazy, and that will put them on edge. If they see you doing anything else they consider different, you may be reported to management, and could lose your job. Everyone has that one guy at work that is always keeping tabs on everyone. listening in to conversations, making silent mental notes of everything he sees or hears (or maybe even keeping spread sheets; who knows?). THIS guy is a prime threat if stuff hits the fan. At work you also have your circle of work buddies, that you tell that the kids have got the sniffles, or that your wife has been nagging all week. Casual chit chat to fill in the time on break, but as you know them longer, you inadvertently reveal more and more personal details, because you don’t usually consider them to be a threat to anything but your potential job security.
If you invite coworkers over for a weekend barbecue or a business get together, be sure to clean up a little more than usual. Lock doors to rooms that do not need to be entered (pretty much all rooms except the bathroom or kitchen), and conceal or temporarily remove anything that may let them in on the fact that you are a prepper or survivalist. Putting up the survival magazines, Locking away your firearms, and temporarily moving things like gas masks and bug-out bags that may be waiting at your front door into a locked room is advisable.
Occasionally we have to let people that we do not know at all have access to our personal information. These are the casual acquaintances that comprise the fifth inner circle. You may think they are so far removed from the inner circle that they pose no threat, but attention to detail and restricting what you do and say in their presence is still advisable.

EXAMPLE:
The repairman that has to fix something upstairs inadvertently walks past something you forgot to put away. Being given access to the interior of your home gives them the exact layout of your floor plan, and potentially your interior security systems. Always have somebody at home to let them in, never give them a key as it takes just seconds for them to make a mold to duplicate later. Many burglars also use the guise of being repairmen or professional movers to break into peoples homes in the middle of the day, as they go unnoticed by the neighbors. Always hiring people that are licensed, bonded, insured, and well reviewed by third parties will lower the risk.
OR:
The mailman that sees your wide assortment of outdoors catalogs, and obviously knows where you live. Being an employee of the government, they may be asked to report on suspicious activity, and given a list of things to look out for that may get you in trouble before you ever get a chance to put your preps into practice. Several documents have come out over the years listing different characteristics and indicators to look for when profiling potential “terrorists”. Some of the targets have included such innocuous acts as taking photographs or video, writing on paper, and even supporting certain political candidates. Even renting a private mail box doesn’t mitigate the risk much, as you are required to register the box in your legal name and give your physical address on the application.
The sixth and final circle of trust deals with everybody else you come in contact with. From the person that looks at you when you are stopped at the red light, to the couple in the next booth at the restaurant, to your neighbor down the street that waves hello to you as you drive past. What will your response be when you are buying several 30 pound bags of rice and the cashier wants to strike up a conversation about it? Always have a cover story no matter how much of a stranger you think the person is. When shopping for preparedness supplies, try to shop at 24 hour stores so that fewer people are around, and pay cash to avoid leaving an electronic paper trail. It is also advisable to wait until trash day to discard the packaging for any prepper supplies, and to bag them separately from anything that may have your name or address on it.
When you are out in public sizing up a new place by counting exits, noticing the position of cameras, analyzing potential threats etc., you don’t want to be noticed. Become a people watcher, learn body language, and study the works of scientists such as Paul Ekman, to become a better read of peoples emotions and honesty. Knowing things like the difference between somebody smiling when they are happy or when they are uncomfortable is very important. Master the art of mimicry, for example if they smile, you smile, or if they want to make small talk, make small talk. Be polite but casual. Don’t oversell anything, and leave out the details. Obviously if the person is exhibiting offensive behavior it is better not to mimic, but to disengage without confrontation.
This article has covered some, but not all, of the steps you can take to protect your operations security. Through identifying critical information, analyzing potential threats and vulnerabilities, assessing those risks, and then applying countermeasures to ensure your safety, you can improve your odds of protecting the secrecy of your preparations. Following the steps and ideas discussed in this article will help you be well on your way to protecting your privacy. If you found this article informative, think twice about it’s implications to your own personal operations security before sharing it.
